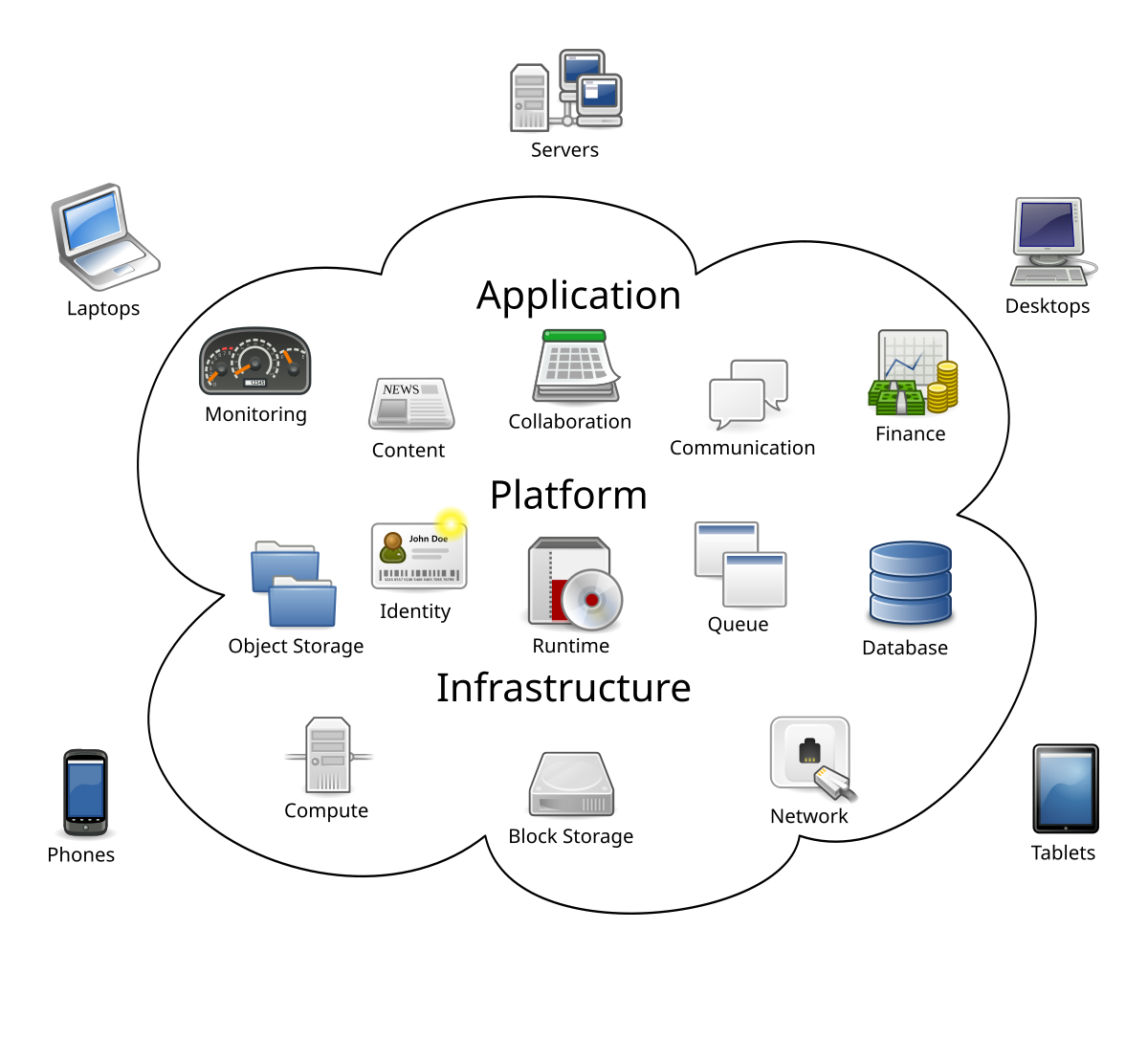
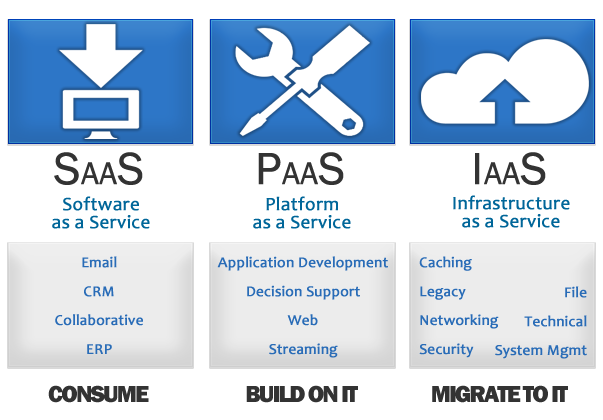
Why Learn Linux
Linux was introduced by Linus Torvalds, in 1991. It was released under GNU GPL, with the help of the support free Software Foundation (FSF) helps Linux confirmed as a very low-cost operating system also almost free OS. Though Linux prompt as a server OS, it has finally advanced into diverse platforms, like computer systems to notable computers. Linux has additionally discovered its location in embedded gadgets and lately in handheld gadgets, with the launch of Android.
With the increase of Linux server market, in addition to the with embedded and cellular Linux markets, call for Linux professionals has additionally grown immensely. And that is the proper time for IT professionals to embody Linux and open source.
Pro’s of Linux Training in Chandigarh
Linux is being carried out in each conceivable platform, due to the fact its multifaceted benefits had been confirmed over time.
Freedom: Linux and lots of its software program are open supply and all of us may also personalize it, meet their very own requirements. Freedom to recognize the OS from inside, may even assist to apply it higher and construct higher software program. Also, the outstanding wide variety of Linux distributions provides freedom of choice.
Lower costs: The GNU GPL license of Linux and a enormous range of its software program appreciably brings down the price factor.
Stability and Performance: Linux may be appropriate for any sort of hardware, even the older ones. It is designed to scale up for huge concurrent utilization and is until with ease maintainable. Memory leaks and the likes seldom influence Linux's overall performance and stability.
Flexibility and Compatibility: Linux is simply proper for any type of platforms might also additionally or not it's a server or computer or embedded device or maybe a amazing computer. There is limitless freedom to put in best sure additives that match the requirements. Also maximum document codec’s may be processed on Linux and lots of a UNIX software program is like minded with Linux.
Network friendliness: Network capability is middle to Linux and it's far very a great deal best for a dispensed paintings environment. Tasks like management and backup can without difficulty be executed over networks.
Multitasking: Various duties may be concurrently undertaken via way of means of Linux installations. Heavy framework methods not often slow down foreground duties.
Security: Security is a sparkling spotlight of Linux and it might be the maximum secure, famous OS. Linux usually a trouble-unfastened machine and regulations may be set to manipulate customers and get entry to on a granular level.
Linux Courses & Boot Camps
At Cbitss Technologies, various Linux training courses are available. We are an Authorized Training Partner of Red Hat; the education will be basically focusing at the RHEL platform. The Linux guides to be had and the contents of every indexed below.
Course: Linux Administration
Modules:
• Linux Essentials
• Linux System Administration
• Linux Network & Security
Course: Linux Virtualization
Modules:
• Linux Enterprise Virtualization
Course: Linux Security
Modules:
• Enterprise Network Services Security
• Directory Services and Authentication
• SELinux Policy Administration
Course: Datacenter Administration
Modules:
• Deployment, Virtualization, and Systems Management
• Clustering and Storage Management
• Directory Services and Authentication
Course: Linux Enterprise Architecture
Modules:
• Enterprise Security: Network Services
• Enterprise Deployment and Systems Management
• Enterprise Directory Services and Authentication
• Enterprise Virtualization
• Enterprise Storage Management
• Enterprise System Monitoring and Performance Tuning
Linux Certifications
We are leaders in Red Hat Linux Certification training. Red Hat Linux Certifications are relatively valued within side the enterprise due to the fact they are performance-primarily based totally assessment tests, performed and authorized immediately through Red Hat, within side the presence of a Red Hat Examiner. The Linux Certifications provided are:
• RHCSA - Red Hat Certified System Administrator
• RHCE - Red Hat Certified Engineer
• RHCVA - Red Hat Certified Virtualization Administrator
• RHCSS - Red Hat Certified Security Specialist
• RHCDS - Red Hat Certified Datacenter Specialist
• RHCA - Red Hat Certified Architect
Cbitss leads the Indian marketplace in offering great Linux training to corporates, specialists, and students. Our Linux training specializes in equipping scholars to independently deal with job-stage scenarios. Some of the highlights of our Linux training include:
· Well geared up labs and infrastructure
· Linux Servers for every student
· Experienced college presenting person attention
· The lab primarily based totally expert training
· Special exercise classes for the ones attempting certifications
Book your seat now and join our classes. You can call us 09988741983, or visit us @ Linux Training . Don’t miss the chance of getting training from Cbitss Technologies experts.